AMSECT Mifare Security Tool
AMSECT (AMSECT Mifare Security Tool) was designed to demonstrate the weaknesses of Mifare Classic. AMSECT can be used to read and write data to and from Mifare Classic Tags, if the required sector keys are known.Some of the App-Features:
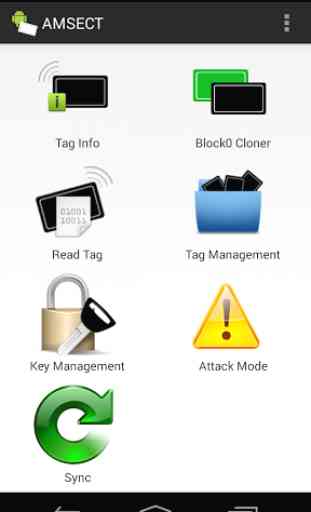
- Tag Info: Display Tag Information and identify vulnerable cards
- Tag Management: Display tag dumps, manipulate and write them to a Mifare Classic tags
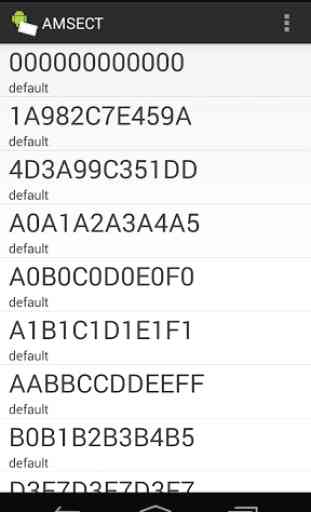
- Key Management: Add Mifare Classic Keys to your app for tag reading and writing
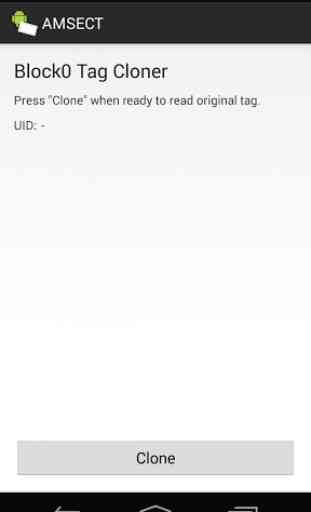
- Block0 Cloner: Clone a tag's UID to a Block0 writeable tag without reading the tag or knowing it's keys.
- Import/Export Options: Share cards and keys with Android Beam, Export and Import from filesystem or use FTP to sync tags (FTP is experimental)
Requirements:This tool requires Mifare Classic Support on the target device. All devices with NXP NFC Chips should work perfectly, the App was tested and developed using Samsung Galaxy Nexus smartphones on Android 4.4.2. Latest Nexus Phones and Tablets are shipped with Broadcom NFC Chips and therefore NOT compatible!
Hints:
* If a sector of a card only consists of 000000000000FF778069000000000000 Blocks, no key could be used to read the sector.
* Block 0 writable Cards seem to be buggy. If the card uses the default key (FFFFFFFFFFFF) in Block 0 and an error is thrown, try again until it works (it might take more than 5 tries).
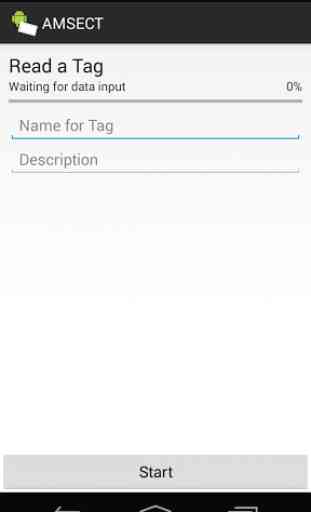
* Attack Mode: Start covered reading of a tag by entering "tag -tag name
- -description-" in the URL box.
- Tag Info: Display Tag Information and identify vulnerable cards
- Tag Management: Display tag dumps, manipulate and write them to a Mifare Classic tags
- Key Management: Add Mifare Classic Keys to your app for tag reading and writing
- Block0 Cloner: Clone a tag's UID to a Block0 writeable tag without reading the tag or knowing it's keys.
- Import/Export Options: Share cards and keys with Android Beam, Export and Import from filesystem or use FTP to sync tags (FTP is experimental)
Requirements:This tool requires Mifare Classic Support on the target device. All devices with NXP NFC Chips should work perfectly, the App was tested and developed using Samsung Galaxy Nexus smartphones on Android 4.4.2. Latest Nexus Phones and Tablets are shipped with Broadcom NFC Chips and therefore NOT compatible!
Hints:
* If a sector of a card only consists of 000000000000FF778069000000000000 Blocks, no key could be used to read the sector.
* Block 0 writable Cards seem to be buggy. If the card uses the default key (FFFFFFFFFFFF) in Block 0 and an error is thrown, try again until it works (it might take more than 5 tries).
* Attack Mode: Start covered reading of a tag by entering "tag -tag name
- -description-" in the URL box.
Category : Tools

Related searches