EAGLE Security UNLIMITED
Here are three main wiring methods described below.
1. Spyware (or Scumware)
The software you install on your mobile phone can tape your phone calls, capture photo and video not only when you talk or use the camera application but in standby mode as well.
Protection: you need to be careful installing new software and check whether it has access to your camera and microphone or not and also to internet, phone calls, SMS etc. Always check the producing company as well if it is trustworthy or not.
Spyware might also be installed on the device without your disclosure. Such apps are prohibited on Google Play. Thus they are usually apps that can only be installed from an APK file, they transmit your location, calls or messages to a person that want to wire you. In the list of the applications they usually look like fishing websites addresses such as ‘Googel Services’, ‘Google Drlve’ with the same app icon as the similar real applications. The package names are also usually very similar to any popular application, so it might be difficult to find them. It might be a collegue, a relative or a phone service technician who may install such an app on a user’s cellphone.
Eagle Security allows you to get the full list of the applications on your device. You can check the permissions they requested and find out which apps require multiple permissions that let them to spy you.
Eagle Security also provides functionality to disable camera and/or microphone on your phone to make it impossible for any spyware to use them when you want to be sure that your phone is not listening or watching you.
This app uses the Device Administrator permission.
2. Substitution of base station
Lately this method has become very popular because IMSI catchers become very cheap and easy to buy. Wiring kit can be placed next to you not far than in 500 meters and all the cell phones in the action radius connect to the fake station due to its powerful signal. IMSI catchers are ofter used with a jamming station to suppress all the cell towers and make all the near phones to register in the network via the IMSI catcher.
Such kits could be not bigger than an attache case and can be easily used without your notice.
Your can’t know that the base station was substituted because the new station transmits all the data to the real one and calls work in the normal way. Everybody can buy such compex at affordable price.
Protection: tracking all the stations your cell phone connects to. Eagle Security checks the signature of a station, mostly tapping complexes have substandard signatures. And it also tracks positions of stations. If a station appears in different places or appears in a new place near to a station placed in the same place before it’d be marked as a suspicious and all the other users will be informed if they connect this station.
Connection to a suspicious base station doesn’t mean that somebody is tapping you for sure. But it’s strongly recommend not to use your phone when it’s connected to untrustworthy base station.
3. The third method
Having contacts in security agencies you can get an official allowance to wire a cell phone. In many countries it’s enough to give a person a witness status in any judicial case. The person will never even know about that because such tapping is formally legal.
Protection: voice and message encryption. You can use software for secured calls and messaging by independent developers such as Telegram.
Eagle Security helps our users to protect themselves from the first and the second methods described above higly efficiently.
With Eagle security you can monitor and explore cell network around you and control access of the applications on your device to your hardware.
Category : Communication

Reviews (18)
Awesome app. Takes research to understand the concept behind it and I'm by no means an expert now but it's enough to get me questioning at least. Recommended - what to do if dodgy tower signals picked up + alert functionality maybe? (despite strain on phone resources). I used the free version for months but decided to go unlimited. If trouble installing unlimited - don't worry about Store cache - deactivate free version through Device Manager, delete free version then Store\Library boom! =]
its scary when you find a red tower but reassuring when you find many greens. very informative in tge facts but it would be great to see some ideas about a course of action to take when red does show up..ways to block, or hide from them so you have confidence that nobody is listening in or recording your calls and texts. thanks
I finally saw this app in action after traveling. There are hidden fake towers everywhere. This is a great app !All i had to do to get on a green tower and stop connecting to red towers is switch to 4g only mode without lte with a 4g switcher app.
What exactly is it supposed to do.? Does it catch hackers ..and fake ARP connections ? Does an alarm ring..or does the fake imsi connection flash or blink on screen. ? What warning is there ? It feels like the app is missing something.. how does one trace a fake Mac address to an actual IP address or GPS location One Fake connection on my network shows on another app...but not on this software it doesn't show It shows on my network as 0000000000 As "Xerox"..but its not a real Xerox Mac number
I never knew the dangers of IMSI catchers and the use of Stingray surveillance were used so frequently by law enforcement. This app is great. A video tutorial showing what to look for would be very helpful as well. Thx EAGLE Security
I paid for this app also and it wouldn't download or refund, and I got no response when I first reviewed. I really love the app and really want the pro version. That gmail email did not work either.
I paid for this app and it will not download! I also tried to email you with the email you provided and that email address dont work. I would like a refund!!
If this app actually works, then I'm totally screwed! Red towers moving around my place constantly.
Had to give 3 cause emailed them bout an issue and still have not heard back from them.
I want to give this a 5 star rating but it won't let me install The pro version. It gets to the end then hangs please advise
Not working for me anymore it just ssd top working
Dont know how to use it not sure what any of it means need info or video
Very good for whats is designed for
In my view this program the best. Many thanks.
Found the people using IMSI catchers on my communications and located there base house. 5 star
Finally a legit app for this.
[email protected] Leavingmyfeedbackmappinggpshomepointmaptime ShowingNetVelocityTowerSignalTestKpiPciDssMccMncAddedDataGpsMap
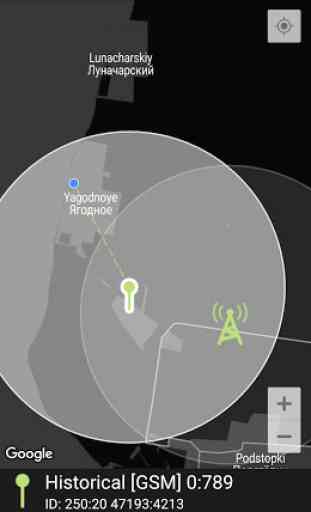
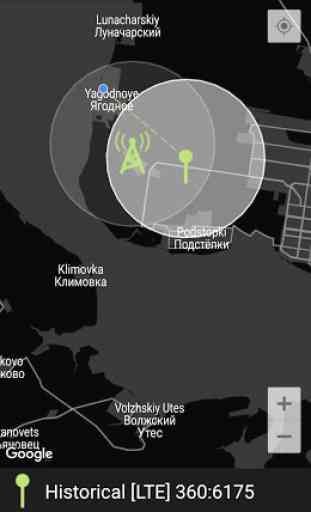
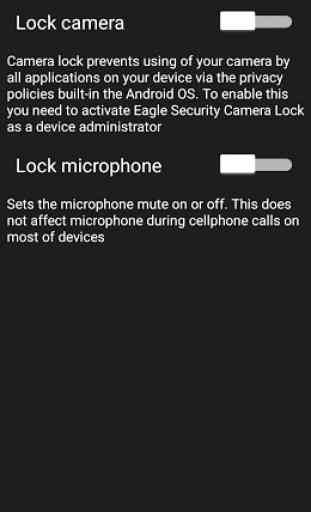
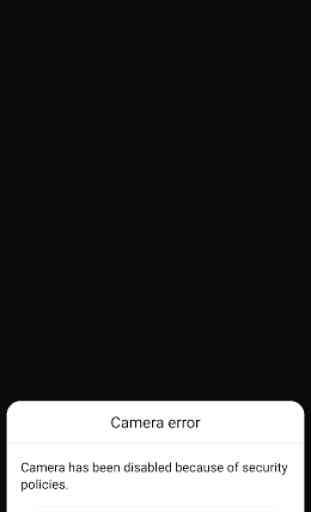

The purpose of this app is to check that your cell phone is connected to a legitimate cell tower as opposed to a fake tower that might be setup by a government entity or criminal snoop to to intercept communications. The app has a couple of other security features (e.g. Lock camera) that might be useful if you're running earlier versions of Android that don't have the permissions manager feature. Noticed the app hasn't been updated since Jul 2019; hopefully it will continue to be supported.