Installer Hijacking Scanner
* [IMPORTANT] To install the dummy app, it requires you to enable the "Unknown Sources" setting (Thank David LaVeque for the reminder). If you did not change the setting before trying the scanner app, your phone may be falsely reported as vulnerable. In this case, please click 'reset' button, and retry the app.
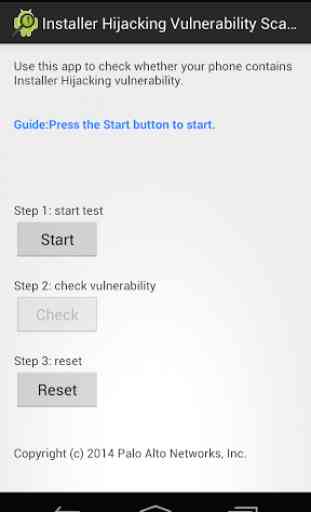
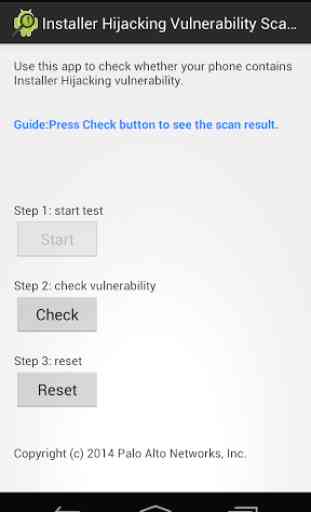
* Please follow the step 1 -> 2 ->3 to finish the scan. Step 1 starts an app installation procedure. Please follow the procedure and install that dummy app. Step 2 helps to check the existence of vulnerability. Step 3 'reset' will remove that dummy app you just installed.
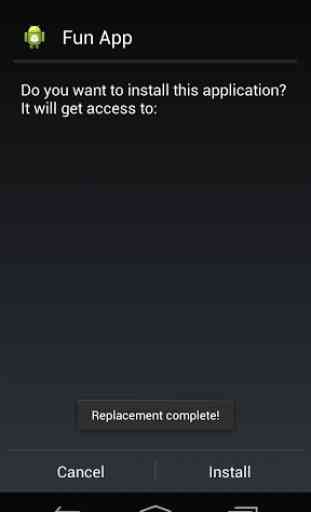
* You may be asked to install an apk file. This is a dummy app with no content. Since this is a OS vulnerability, we have to go through the installation procedure in order to determine if the device is vulnerable or not. This dummy app will be uninstalled when you press the 'reset' button.
* If the device does not contain this vulnerability, the dummy app will not be installed. So, when you press the 'reset' button, the app uninstallation window will not pop up.
* On some devices, after first install, some devices may report error with "Parser Failure". Please restart the app and try again. Copryright: Copyright ©2015, Palo Alto Networks, Inc. All rights reserved. Palo Alto Networks, the Palo Alto Networks Logo, are trademarks of Palo Alto Networks, Inc. All specifications are subject to change without notice. Palo Alto Networks assumes no responsibility for any inaccuracies in this document or for any obligation to update information in this document. Palo Alto Networks reserves the right to change, modify, transfer, or otherwise revise this publication without notice.
Before you start testing on your device, please read the [How-to-use] below. Go through the video bellow will also be greatly helpful. Thanks for your patience.
Briefly, this vulnerability has been patched on Android version 4.4 and up. Devices with Android version 4.3 may contain this vulnerability, depending on vendors. Devices with Android version <=4.2 all have this vulnerability.
Learn more about the vulnerability here: http://researchcenter.paloaltonetworks.com/2015/03/android-installer-hijacking-vulnerability-could-expose-android-users-to-malware/
Demo video:https://www.youtube.com/watch?v=81slOhjrZXYhttps://www.youtube.com/watch?v=AgPEoYdHE34
How-to-use:
* [IMPORTANT] To install the dummy app, it requires you to enable the "Unknown Sources" setting (Thank David LaVeque for the reminder). If you did not change the setting before trying the scanner app, your phone may be falsely reported as vulnerable. In this case, please click 'reset' button, and retry the app.
* Please follow the step 1 -> 2 ->3 to finish the scan. Step 1 starts an app installation procedure. Please follow the procedure and install that dummy app. Step 2 helps to check the existence of vulnerability. Step 3 'reset' will remove that dummy app you just installed.
* You may be asked to install an apk file. This is a dummy app with no content. Since this is a OS vulnerability, we have to go through the installation procedure in order to determine if the device is vulnerable or not. This dummy app will be uninstalled when you press the 'reset' button.
* If the device does not contain this vulnerability, the dummy app will not be installed. So, when you press the 'reset' button, the app uninstallation window will not pop up.
* On some devices, after first install, some devices may report error with "Parser Failure". Please restart the app and try again.
Copryright: Copyright ©2015, Palo Alto Networks, Inc. All rights reserved. Palo Alto Networks, the Palo Alto Networks Logo, are trademarks of Palo Alto Networks, Inc. All specifications are subject to change without notice. Palo Alto Networks assumes no responsibility for any inaccuracies in this document or for any obligation to update information in this document. Palo Alto Networks reserves the right to change, modify, transfer, or otherwise revise this publica
Category : Tools

Reviews (30)
contrary to what articles say; that I should not be affected due to my OS version, my phone can still be infected. I think this app is a joke. UPDATE 3/30/15: after developer update, I tried again and my phone (Nexus 6 now with Android 5.1) would not allow the dummy app to install, so it appears my phone is now safe from any vulnerabilities. I now rate 5 star and thank developer for fixing the app.
Right after I hit the start button it crashes. The message says Scan Stopped then it closes.
It comes up as dummy app, I press install it now says replacement app but it says app not installed.
This app "scans" for the vulnerability by performing it on your phone and then checking if the app had its permissions changed. It's not a scanner in any traditional sense.
This app totally wiped out my tablet cannot boot past start screen. Warning - do not use this app - google should pull immediately.
I love it bcz it save my phone. Thanks a lot Admin n also thanks to Hindustan who tell me about this app.
It first said android 5.1 on my nexus 5 had the vulnerability after the March 26th update then ran the test again and it said I was safe so which is it, am I safe or not also I may point out that my nexus 5 is rooted
How i use this app. How it work plz suggest me early
At first I did the test and the result was my device had the vulnerability. After the press of a few more buttons I ran the test and my device was safe. I simply scanned twice, I didn't enable any protection
This app is not working my galaxy grand prime....
Using a samsung note 3 running android 4.4.2 . It shouldn't have the vulnerability yet this app says it has. Am I supposed to install replacement app?
Won't work. "Can't parse the package" Whatever that means
What to do after detection of vulnerability? Which app is vulnerable? There is no information regarding this. Then what is the use of this app.?
My device is infected or has been hijacked, then what? How can I remove this?
Thanks for this app. ☺😊
I dont soure this app after app loding
This proof of concept app is poorly done, probably not well tested, and actually will tell vulnerable phones that they are safe. Not to be trusted. A security company really should invest in better testing before releasing an app and stirring up some dirt and false claims that some Android versions are safe when it's their terrible app not properly executing the vulnerability.
I read that versions 4.4 and higher aren't affected by the vulnerability. I'm running 5.0 on a 2014 Moto X so from my understanding the "fun app" shouldn't work, but yet it still runs/installs after I hit test
According to info listed, my version 4.4.4 should not be vulnerable, bit their test says it is. I ran it a second time and it said my Moto X 2013 was secure. I ran it a third time and it came up vulnerable again.
It installed and ran fine, but it says I have the vulnerability. Verizon Samsung Galaxy S4 running 4.4.2. This contradicts the app description which says that the vulnerability was patched on version 4.4 and up. Is this an issue with Verizon's 4.4.2 not incorporating the patch, or is this an issue with this particular app not working the way it was intended? I don't know!
It says that Android 5.1 has the vulnerability. A broken security app really undermines the credibility of this security research company.
I am running 4.4.2 on an LG G2 and it still shows that it is vulnerable. Either this program doesn't work or 4.4 is not fixed yet.
To those who are wondering what to do if their device is vulnerable like me,it's better follow the link posted in the description of the app and you will see that there is nothing much you can do about it,only some safety procedures to be followed :'(
To all the people saying it's false is wrong. I did the test and when the Apk try to install it says parsing error. And that wonderfully. Thsnks
Great app! Was able to patch the vulnerabilities Bluebox Security Scanner, and adjust app settings. No vulnerabilities discovered after the patch, excellent app, great work! Running CM11.
Both say the app is safe to install. If this is true why am I even paying for both antivirus program!!!
Though I have 4.4.2 it shows I am still vulnerable.
It might be working but im not really sure.....The app seems to install a note saying "if it installs it has the proposed vulnerability." So does that mean it is installed or not? Your video has a clear message: "Be aware!! This device..." but the actual app does not.
ran test and it's saying that it's vulnerable.. any way to patch it. other then waiting on carrier..

took 4 parse error attempts on 4.4.4 to install replacement app and said vulnerable. tried older JB and ICS phones instantly installed replacement app and reported being vulnerable. I use xprivacy and droidwall so even if I do get snared the app still wouldnt get to use switched permissions without knowing. - - - - - reading the comments from others that are just so clueless and can't read the description information or understand the instructions should only use Google play because no app fixes ignorance.