SSH Two-Factor Authentication
This Application is designed for SSH Two Factor Authentication.
Easy and Secure way to protect servers from unauthorized access.
WARNING:
** For: System-Administrators
** Needs 3rd party Software to be installed
Please note that this application requires internet on both side for full feature.
About the application:
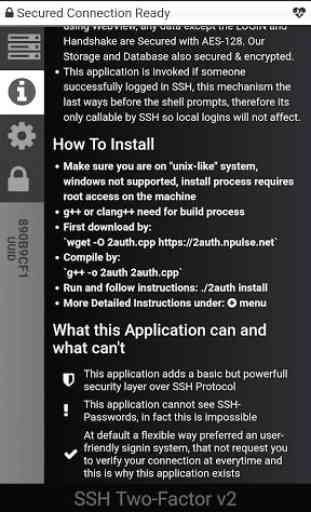
- This is application is intended to a second-level security top on SSH access.
- Therefore this application invoked if a successfully login made through SSH.
How is it work?
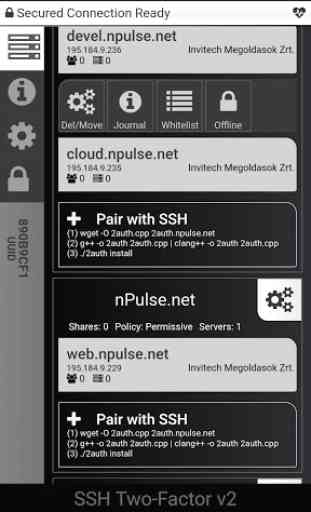
- You only need to compile and install one .cpp file, then one extra line at end of sshd_config file.
- Once a successfully SSH login made the binary file invoked and temporarily replaces any shell, so the two factor mechanism starts at this point.
- Simply open your app in your phone and the permission will be asked by prompt.
According to GDPR rules and other privacy policy, that you can read detailed below, this service may store private informations such as phone model, datetime, login attempts, ip address and email account. We store informations highly secured and encrypted. Also we uses hard encryptions please make sure you that your country allowing use of encryption.
Features:
- Work with any type of shell, supports sftp and rsync as well.
- Logging any login attempts
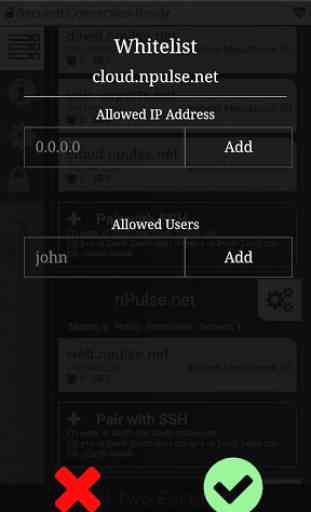
- (new) Grouping, you can now share the whole group between accounts
- (new) 3 types of authentication mechanisms, Permissive, Strict, Disabled
- Permissive: Allow now and for last 6 hours any type of login with same IP and Group.
- Strict: Always needs verification
- Disabled: Two-Factor Authentication disabled but logged.
- This application technically can not see any SSH passwords.
- However this application is top of SSH layer but totally independent so cannot be use as backdoor and does not replace any SSH functions.
Why is this very usefull?
- 99% of successfull 'ssh-break-in' attack can be mitigated
- Logs. and these kind of logs are independent.
- Does not slow you down, you don't need to be authenticated all time
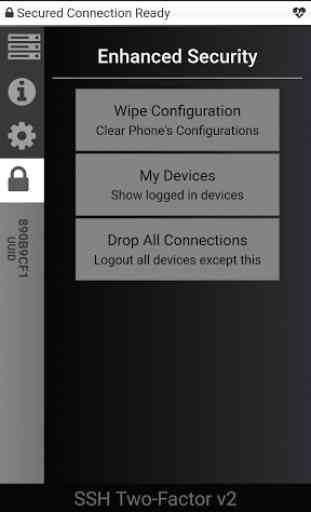
- Account based authentication so if you lost your device just login again
Always write-down your emergency keys and test it to avoid lockout yourself.
There is a Offline Authentication if you have network issues by time challenge which can be adjusted.
** Attention, this software currently in BETA phase, it may contains bugs **
Easy and Secure way to protect servers from unauthorized access.
WARNING:
** For: System-Administrators
** Needs 3rd party Software to be installed
Please note that this application requires internet on both side for full feature.
About the application:
- This is application is intended to a second-level security top on SSH access.
- Therefore this application invoked if a successfully login made through SSH.
How is it work?
- You only need to compile and install one .cpp file, then one extra line at end of sshd_config file.
- Once a successfully SSH login made the binary file invoked and temporarily replaces any shell, so the two factor mechanism starts at this point.
- Simply open your app in your phone and the permission will be asked by prompt.
According to GDPR rules and other privacy policy, that you can read detailed below, this service may store private informations such as phone model, datetime, login attempts, ip address and email account. We store informations highly secured and encrypted. Also we uses hard encryptions please make sure you that your country allowing use of encryption.
Features:
- Work with any type of shell, supports sftp and rsync as well.
- Logging any login attempts
- (new) Grouping, you can now share the whole group between accounts
- (new) 3 types of authentication mechanisms, Permissive, Strict, Disabled
- Permissive: Allow now and for last 6 hours any type of login with same IP and Group.
- Strict: Always needs verification
- Disabled: Two-Factor Authentication disabled but logged.
- This application technically can not see any SSH passwords.
- However this application is top of SSH layer but totally independent so cannot be use as backdoor and does not replace any SSH functions.
Why is this very usefull?
- 99% of successfull 'ssh-break-in' attack can be mitigated
- Logs. and these kind of logs are independent.
- Does not slow you down, you don't need to be authenticated all time
- Account based authentication so if you lost your device just login again
Always write-down your emergency keys and test it to avoid lockout yourself.
There is a Offline Authentication if you have network issues by time challenge which can be adjusted.
** Attention, this software currently in BETA phase, it may contains bugs **
Category : Tools

Related searches