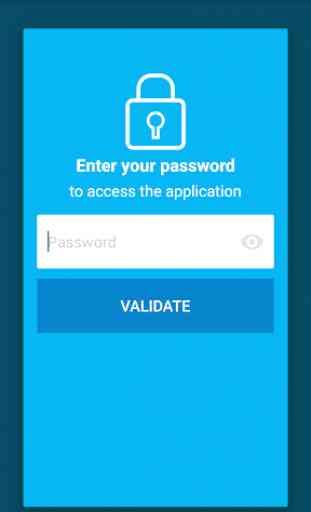
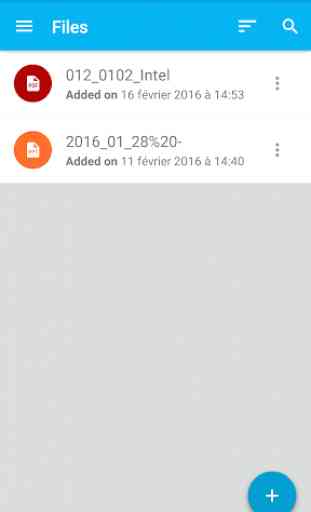
Stormshield Data Security (SDS)
SDS for Cloud & Mobility application allows you to collaborate and to exchange confidential information more securely anywhere and from any devices. It makes it possible to encrypt data before sharing it through cloud platforms such as Onedrive, Dropbox, Oodrive etc.
It offers you the best end to end encryption experience and empowers your users to collaborate securely inside and outside the company.
Available features:
• Available for any devices, computers, smartphones, tablets
• Robust encryption using AES and RSA keys
• Support of cloud platforms such as Dropbox, Onedrive, Sharepoint, Oodrive, etc.
• No deployment needed on the cloud platform which is only used as a storage space and has no knowledge of the content of your confidential data
• Various authentication methods supported: password, biometrics, smartcard or cryptographic token
• Smartcard compatibility to use the private key on it (Gemalto/SafeNet compatibility)
For the user:
• Smart tutorial to improve the usability of the solution
• Adaptive view when you want to use the application on a tablet
• View your encrypted documents from your devices: Word, PowerPoint, Excel, PDF, pictures, videos, etc.
• Protect your work documents, photos and videos: all files are stored securely and can only be accessed in the Stormshield Data Security application via a password or strong authentication.
• Get your authentication file from other apps (e.g., Dropbox, OneDrive)
• Your private key can be stored directly in the application. It is protected by a password or strong authentication and allows you to access your encrypted data
For the Administrator:
• SDMC (Stormshield Data Management Center) SaaS Cloud Administration console on https://sds.stormshieldcs.eu
• SDMC Administration console On Premise
• PKI compatibility
• Centralized dashboard
• Enforce security by applying security rules (e.g., type of authentication, application password strength)
• Lock the application remotely if needed depending of the geolocation
• Export of all the logs to a SIEM (On Premise only)
• Beta features:
o Built-in key management, no PKI needed to generate the end user keys
o Easy deployment of the keys on all devices through an enrollment process
o The SDMC server has no knowledge of the key and never stores the password. The key is generated on the end user side
It offers you the best end to end encryption experience and empowers your users to collaborate securely inside and outside the company.
Available features:
• Available for any devices, computers, smartphones, tablets
• Robust encryption using AES and RSA keys
• Support of cloud platforms such as Dropbox, Onedrive, Sharepoint, Oodrive, etc.
• No deployment needed on the cloud platform which is only used as a storage space and has no knowledge of the content of your confidential data
• Various authentication methods supported: password, biometrics, smartcard or cryptographic token
• Smartcard compatibility to use the private key on it (Gemalto/SafeNet compatibility)
For the user:
• Smart tutorial to improve the usability of the solution
• Adaptive view when you want to use the application on a tablet
• View your encrypted documents from your devices: Word, PowerPoint, Excel, PDF, pictures, videos, etc.
• Protect your work documents, photos and videos: all files are stored securely and can only be accessed in the Stormshield Data Security application via a password or strong authentication.
• Get your authentication file from other apps (e.g., Dropbox, OneDrive)
• Your private key can be stored directly in the application. It is protected by a password or strong authentication and allows you to access your encrypted data
For the Administrator:
• SDMC (Stormshield Data Management Center) SaaS Cloud Administration console on https://sds.stormshieldcs.eu
• SDMC Administration console On Premise
• PKI compatibility
• Centralized dashboard
• Enforce security by applying security rules (e.g., type of authentication, application password strength)
• Lock the application remotely if needed depending of the geolocation
• Export of all the logs to a SIEM (On Premise only)
• Beta features:
o Built-in key management, no PKI needed to generate the end user keys
o Easy deployment of the keys on all devices through an enrollment process
o The SDMC server has no knowledge of the key and never stores the password. The key is generated on the end user side
Category : Productivity

Related searches