TNX One Touch
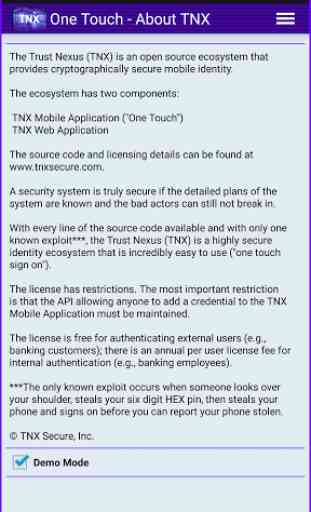
Imagine a world where user names and passwords are no longer necessary, and authentication is simple and secure.A system is secure if the plans for the system are public, and the bad actors can still not break in.The Trust Nexus is the first open-source platform for secure mobile identity:
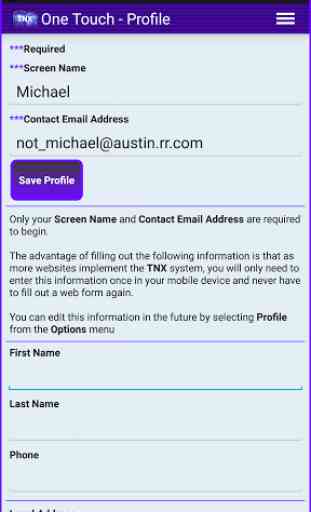
•Consumer Friendly ~ Users touch one button on their mobile device to authenticate to both web based and mobile applications.
•Cryptographically Secure ~ Even if a user's mobile device is lost or stolen his/her credentials are secure (no password based encryption processes; no dependency on "phone lock" OS processes).
•Simple ~ The source code is crystal clear and easy to implement (Android and J2EE; other platforms coming soon).
•Effective ~ We completely do away with user names and passwords and all of their weaknesses.
•Low Cost ~ Our technology and infrastructure services are FREE for every publicly facing website for general user authentication. There is a nominal licensing fee for corporations and government agencies for internal authentication (e.g., free for banking customers; a small annual fee for banking employees).
•Also secures three party credentials (passports, driver's licenses, insurance and financial credentials).
•Eliminates fraudulent financial transactions.The essence of our process is incredibly simple: Through secure mobile identity, we completely do away with user names and passwords (and all of their weaknesses). If a credential is provisioned to a user's mobile device in a valid institutional process, then when the user presents the credential (either in person or over the network)the receiver can be certain that either the credential and the user are valid or the user gave his/her mobile device and six digit HEX pin (1/16,777,216) to someone else.Under the Trust Nexus it truly does not matter who you are; what matters are institutional validations and the ability to verify those validations.Most authentication schemes depend on securing private data; we focus on the ability to use credential data in a valid institutional process. The concept of verifying institutional validations rather than securing private data requires a shift in perspective. Once that mental shift occurs everyone is amazed at how simple our system is.While the Trust Nexus may "defy conventional wisdom", we are confident our core ideas are "non-consensus and right".
•Consumer Friendly ~ Users touch one button on their mobile device to authenticate to both web based and mobile applications.
•Cryptographically Secure ~ Even if a user's mobile device is lost or stolen his/her credentials are secure (no password based encryption processes; no dependency on "phone lock" OS processes).
•Simple ~ The source code is crystal clear and easy to implement (Android and J2EE; other platforms coming soon).
•Effective ~ We completely do away with user names and passwords and all of their weaknesses.
•Low Cost ~ Our technology and infrastructure services are FREE for every publicly facing website for general user authentication. There is a nominal licensing fee for corporations and government agencies for internal authentication (e.g., free for banking customers; a small annual fee for banking employees).
•Also secures three party credentials (passports, driver's licenses, insurance and financial credentials).
•Eliminates fraudulent financial transactions.The essence of our process is incredibly simple: Through secure mobile identity, we completely do away with user names and passwords (and all of their weaknesses). If a credential is provisioned to a user's mobile device in a valid institutional process, then when the user presents the credential (either in person or over the network)the receiver can be certain that either the credential and the user are valid or the user gave his/her mobile device and six digit HEX pin (1/16,777,216) to someone else.Under the Trust Nexus it truly does not matter who you are; what matters are institutional validations and the ability to verify those validations.Most authentication schemes depend on securing private data; we focus on the ability to use credential data in a valid institutional process. The concept of verifying institutional validations rather than securing private data requires a shift in perspective. Once that mental shift occurs everyone is amazed at how simple our system is.While the Trust Nexus may "defy conventional wisdom", we are confident our core ideas are "non-consensus and right".
Category : Business

Related searches